Google Gemini Advanced Now Free for Students – How to Access It
U.S. college students can access advanced AI tools for coding and research for free, enhancing their skills and productivity.
Read more
All Articles
What Is Broken Function-Level Authorization & How to Prevent It
Explore the ins and outs of Broken Function-Level Authorization and learn effective strategies to safeguard your APIs against this critical vulnerability.
Broken Function-Level Authorization
10 LLM Security Tools
Explore essential security tools designed to protect Large Language Models from vulnerabilities like prompt injection and data leaks.
LLM security
API Attacks: Real-World Examples, OWASP Risks & Prevention
Learn the most common API attacks, real-world breach examples, OWASP Top 10 risks, and practical defenses to secure APIs end-to-end.
API attacks
Top 12 Vulnerability Scanning Tools
Explore the top vulnerability scanning tools essential for identifying and mitigating security risks in software, networks, and systems.
vulnerability scanning
IAST vs. DAST: Some Key Differences, Pros/Cons & How to Choose
Explore the key differences, pros, and cons of IAST and DAST in application security testing to choose the best approach for your needs.
IAST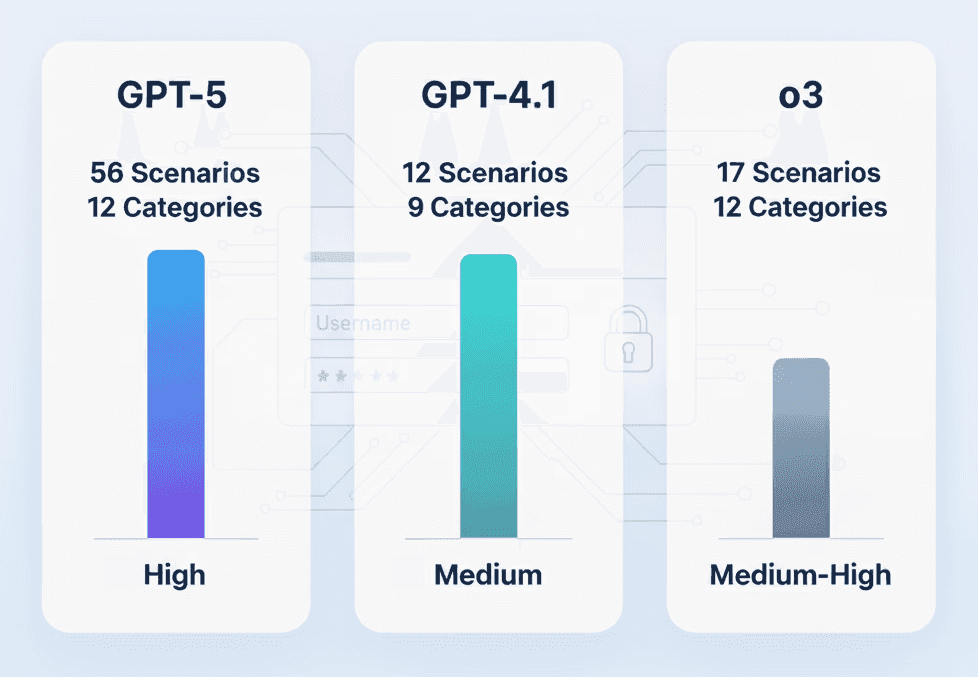
GPT-5 vs O3 vs GPT-4.1, Which one is better for Penetration Testing
Compare GPT-5, O3, and GPT-4.1 for penetration testing. Discover which AI model delivers the best results for ethical hacking.
GPT-5 penetration testing
What Is Burp Suite, and 10 Burp Suite Alternatives and Competitors
Explore Burp Suite and its top 10 alternatives for web application security testing, including features, pricing, and integrations.
Burp Suite
What Is OAuth 2.0 and How Does It Work?
Explore OAuth 2.0, a secure framework for app access to user data, ensuring privacy through token-based permissions and limited scopes.
OAuth 2.0
Top 10 DAST Tools for 2025
Explore the top DAST tools of 2025 for effective API security testing, integration, and automation in modern development workflows
DAST tools
Business Logic vs App Logic: Explained for Developers
Learn how to effectively separate business logic from application logic to enhance software maintainability, scalability, and security.
business logic
Top 10 Cybersecurity Challenges Facing FinTech in 2025
Explore the critical cybersecurity challenges FinTech companies face in 2025, including data breaches, insider threats, and AI-driven attacks.
cybersecurity
API Security Checklist 2025: 12 Steps Every Developer Needs
Follow this 12-step API security checklist (2025 edition) with threat modeling, real examples, PDF, and best practices for robust API protection.
API security